2 Users and Groups. Security
Disclaimer |
|
|
Best PracticeLIMS Roles can be assigned directly to users, or they can be added to groups to inherit group roles. The latter is best practice as all similar user authorisations, e.g. that for Labclerks, can be maintained centrally. Users may belong to more than one group and groups may have overlapping authorisations SecurityBika Inherits its strong security from the framework it is built on, Plone, trusted by the European Union Agency for Cybersecurity, ENISA, many universities, the European Environment Agency, the German Aerospace Center, DLR and more. They use Plone |
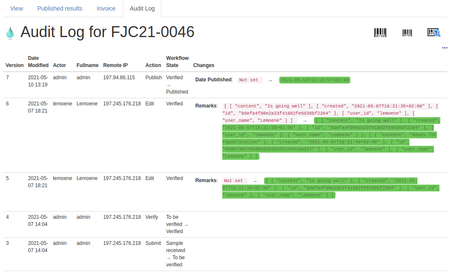
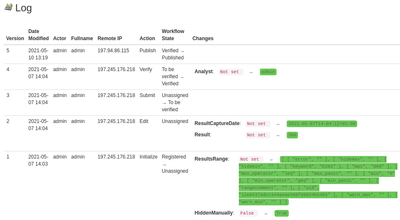
TraceabilityThe underlying web server logs are surfaced to authorised users on all objects' Log tab, their transitions, date/time and user stamp to provide a complete audit trail. For a Sample: To see a specific Analysis' log, navigate to it on its parent Sample, and click the blue information icon on it. It'll pop up a page of all the Analysis' information, including its audit trail at the bottom of the page |
|